Trend Forecasting: How to spot the next big thing in cyber crime?
In this blog post, we will discuss how to forecast the evolution of cyber crime landscape. We’ll first examine the underlying drivers of market, and discuss two powerful techniques for envisioning future scenarios. By understanding the forces at play and applying analytical methodologies, analysts can gain valuable insights into the market’s potential evolution.
Drivers for demand
There are four very common ways a cyber criminal can make money:
- Extortion: Criminals can try to extort money from companies by launching DDoS attacks, encrypting their files with ransomware, or threatening to release sensitive data that will lead to loss of reputation, regulatory fines etc. for the company.
- Selling of commodities: Criminals may try to sell the goods that they obtained such as customer databases, premium accounts, coupon codes, credit cards, bank accounts or sensitive documents. It is a quick way for attackers to make money with less risk if the commodity has a high demand.
- Providing services to facilitate others: While a campaign itself may seem technically simple and straightforward, the process from preparing the attack to cashing out can be long and grueling. Knowing this, criminals can offer services to other hackers that will facilitate some part of their campaigns. This is the most diverse market in the true sense. Some examples; advertising, malvertising, affiliate services, cc checkers, cash out and drop shipping services, crypto laundering, bullet proof hosting, crypters, hash crackers, ready-to-use toolkits, ddos as a service, initial access brokers, 2fa bypass… and the list goes on and on :D
- Utilization of computing resources: Criminals can sometimes utilize the processing power of the systems they have compromised. This can create a decent amount of income with a botnet large enough. Clicking on ads, inauthentic video views/app downloads, generating website traffic, increasing social media followers, and most famously crypto mining are some of the examples.
Once we understand the ways criminals make money, we need to focus on the underlying causes. Without demand, there is no supply. What is produced must be consumed. Let’s take a look at the types of consumers that underlie these markets, which are the true drivers of the demand.
Customers not willing to pay for products or services
It is well known that there are people who want to use products and services without paying for them. The more popular a product is, the more people want to use it for free. This creates a demand that will lead to the natural formation of a market. Think of the Netflix accounts, Amazon coupons, Steam gift codes, premium VPNs etc. that are being sold on the underground markets. Some markets even offer paying your bills with a stolen credit card for a low fee (e.g: 10% of the bill amount). This is by far the largest market in terms of quantity.
Companies engaging in illicit marketing practices
When you think of stolen customer data, first thing that comes to your mind might be identity theft. But the biggest consumers of such data are actually other companies that want to market their own products (and by extension, marketing firms). Instead of curating their own leads, they will take the shortcut and illegally purchase customer data of a company similar to them.
Criminals looking to facilitate their operations
As mentioned before, criminals may need help at some stages in the end-to-end execution of a campaign. They can purchase certain services to scale their campaigns more effectively. This creates a tertiary sector where cybercrime-related services abound. These services are often designed to supplement cybercriminals’ lack of expertise in certain areas.
Companies not willing to take responsibility for a breach
For companies, disclosing a breach is a financial decision as well as a technical one. Damaged reputation, loss of customers, drop in share prices, and regulatory penalties are some of the direct financial losses that may occur. Certain investments and preparations can significantly reduce this risk. Nevertheless, some companies that don’t take these steps may want to avoid the consequences when caught off guard.
How trends emerge?
Based on my observations, there are four ways in which a trend can emerge.
Market innovation
This is the market’s way of solving a bottleneck by developing new products or services. It can result in a new market or enhancement of an existing one. For example, the market has responded to law enforcement pressure on ransomware by developing the Ransomware-as-a-Service. Another example is the emergence of initial access brokerage and infostealer markets to assist others in scaling their campaigns.
As an analyst, watch out for developments that shrink a market significantly. Soon you can expect a market innovation to happen there. Because people(criminals) are less likely to give up on the ways they are used to for making money. Instead, they will seek ways to overcome the obstacles. If the pressure on a market is too much, sometimes you will find that the market begins to consolidate in the hands of the big players. This is simply what has happened to the stolen credit card market over the past few years.
Technological advancement
Whenever there is a technological breakthrough, attackers will look for ways to exploit it. For example, the introduction of bitcoin into our daily lives has given birth to cryptominer botnets and ransomware. Similarly, the increasing role of smartphones in our daily lives has led criminals to start targeting these platforms as well.
As an analyst, when you become aware of a new mainstream technology, adopt an adversarial mindset to identify the opportunities with it.
Changes in demand
Sometimes events occur that lead to a change in consumer behavior. Often the market follows this change in demand. For example, the demand for online products and services spiked during the Covid. This was due to people spending significantly more time at their homes. Cybercrime markets have followed suit, with an increase in credential stuffing attacks.
As an analyst, we have to keep an eye on the consumer habits, as they may have an influence in the cyber world as well.
Cross transference
Trends usually start in a single market and then spread to the others. For example, mobile malware was already used in the US market before it became a trend in the Turkish market. If you have visibility into cybercrime ecosystems around the world, you can keep a close eye on the trends you observe in one of them.
Thinking of possible futures
Having grasped the dynamics of market forces, I would like to discuss two techniques for envisioning future scenarios. Essentially, our objective is to make predictions about how the market may develop given specific factors.
1. User journey mapping to identify new market opportunities
User journey is a term borrowed from the field of UX research. It means a path a user may take to reach their goal when using a particular website. Once a user journey has been mapped, insights are gained for pain points and opportunities. These insights are then used to design the feature that will enable the user to achieve their goals more easily.
In our case, users are cybercriminals and the journey is the path they follow to achieve their goal of making money. To begin, select a user persona and try to list all the steps and methods they employ. Next, consider their potential pain points, as each one can reveal opportunities for a new market. By adopting this entrepreneurial approach, you can identify potential services that may emerge in the future.
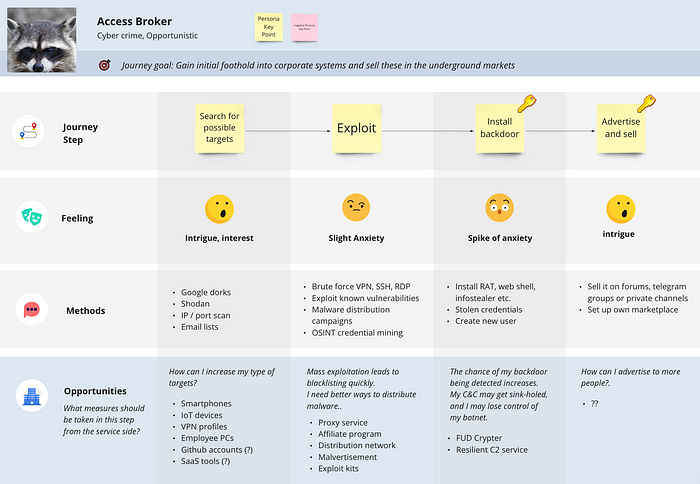
2. Cone of plausibility to forecast impact of events
Before diving into the topic, I highly recommend you to read the following blog posts. They make great explanations of the concept with practical examples.
Now quoting from the first article:
Cone of Plausibility is a structured analytic technique that can be used by intelligence analysts to generate possible threat actor scenarios based on known drivers and events.
By gaining a thorough understanding of the market drivers, it becomes easier to anticipate the impact that any change could have on that particular market. Here is an example that explores the consequences of legal and technical measures implemented to combat credit card theft within this market.
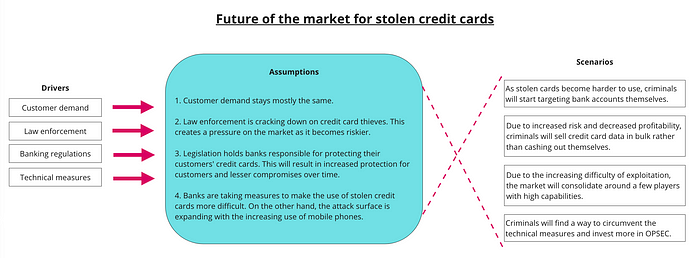
As you can see, the listed scenarios demonstrate realistic possibilities for the future trajectory of the market. As an analyst, we can try to observe the early signs of each scenario.
Cultivating the indicators
After engaging in extensive brainstorming regarding market opportunities and potential future scenarios, it is essential to consider the early signs that can be observed if a scenario were to materialize. After a scenario has been laid out clearly and concisely the early signs become apparent. When choosing our early indicators it is important to ensure that they are feasible to observe. There should also be distinctive indicators for different scenarios so that we can differentiate them.
Once we have identified the early signs, it is time to observe them and wait for our predictions to come true.
I hope you found this blog post useful.
See you in the next one!
