CTI Playbooks: Cyber crime intelligence
Hello everyone!
In this blog post, I will be sharing my personal playbook, which serves as a guide to conducting thorough and effective cyber crime intelligence research. This playbook outlines the step-by-step process I follow, highlighting the intelligence requirements associated with each stage. By the end of this article, we will delve into approaches to building an Early Warning System (EWS) with practical examples, using the insights gathered throughout the research process. Whether you are an aspiring cyber threat analyst or a seasoned professional, this playbook will equip you with the tools and insights to navigate the intricate realm of cyber crime intelligence. Let’s dive in!
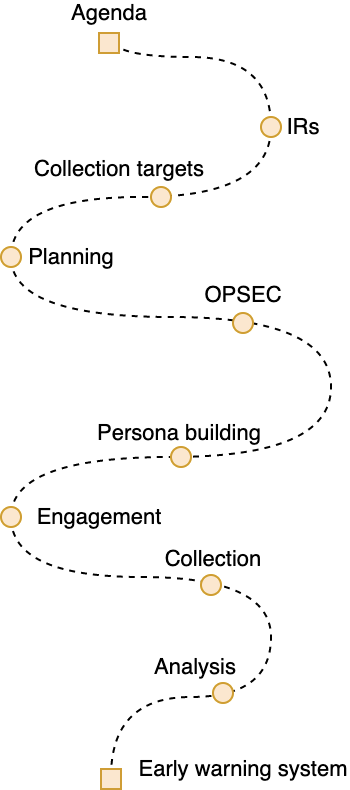
Research of Communication Channels
The initial phase of cyber threat intelligence involves extensive research into the various mediums used by cybercriminals to communicate and orchestrate their activities. The objective of this research is to compile a comprehensive inventory encompassing diverse categories of marketplaces, including forums, Facebook groups, Telegram/ICQ channels, Discord servers, and more.
The following intelligence requirements can be employed to capture essential details about each marketplace, contributing to the comprehensive inventory:
Intelligence requirements:
- How many registered members does the channel have?
- How many members are actively engaged in the channel?
- How many topics or messages are generated within a certain time frame?
- What is the primary purpose of the channel? (e.g., commerce, hacktivism, advertisement, entertainment)
- Are there any specific themes associated with the channel? (e.g., political, religious, nationalistic)
Assessment of Mediums’ Strategic Value
A meticulous evaluation is conducted to determine their strategic value. This assessment allows for the prioritization of mediums based on their significance in facilitating cyber threats and criminal activities.
Intelligence requirements:
- How many successful trades are conducted within a certain time frame, if applicable?
- Estimated trade volume within a certain time frame, if applicable?
- Provide a list of noteworthy activities, such as public breaches of prominent corporations or government entities, along with the responsible threat actors involved.
Market Analysis and Continuous Monitoring
The next step is to gain a comprehensive understanding of the commercial activities within a given marketplace, specifically what types of goods, services, or items are being traded.
Intelligence requirements:
- What types of markets are available, and what items are being traded, if applicable?
- Are there any sub-forums, sub-channels, sub-groups, or units within the channel?
- What are the most prominent activities, services or markets?
Identification of Valuable Targets
In addition to understanding the communication mediums, it is essential to identify and profile the key suppliers within the cybercriminal ecosystem. This process involves uncovering the individuals, groups, or organizations that provide critical resources, such as exploit kits, malware-as-a-service, or stolen data, to threat actors.
Intelligence requirements:
- For each market, who are the consistent suppliers, if applicable?
- Who are the major buyers, if applicable?
- Who are the escrows, if applicable?
- Who is involved in the management?
- Who usually resolves disputes between members?
- Who are the respected members?
- What is the relationship between these people, in form of a relationship matrix?
Creation of a “Watchlist” for Key Threat Actors
A dynamic “always watch” list is established, featuring prominent threat actors who pose a significant risk. This watchlist allows for continuous monitoring and proactive response to the activities and operations of these high-profile cybercriminals.
Intelligence requirements:
- Who is responsible for operating distribution networks or botnets, if applicable?
- Who provides advertisement services, if applicable?
- Who offers bullet-proof hosting services, if applicable?
- Who provides malware distribution or ransomware affiliate services, if applicable?
- Who supplies exploit kits, if applicable?
Digital Footprint Analysis of Threat Actors
Thorough investigation of the digital footprints left behind by threat actors is carried out to compile a set of observables. The more traces we have on an actor, the easier it is for us to track their future movements. These observables will form an important part of our early warning system.
Intelligence requirements:
- What aliases has this actor used and in which channels?
- What email addresses have been identified as being used by this actor?
- What other contact information has been associated with this actor?
- What domain names or IP addresses have been identified as being used by this actor in the past, such as for phishing purposes?
- What SSL certificates or PGP keys have been identified as being used by this actor in the past?
- What social media accounts have been identified as being used by this actor?
- Does the actor utilise any non-hacking related websites, such as Stack Overflow?
Identification of Methods and Tools
To better understand the tactics and techniques employed by cybercriminals, a study of their past activities is undertaken. This includes the collection and analysis of malware samples and exploit kits. By doing so, we not only gain valuable insights for incident response but also identify important patterns that serve as potential observation opportunities for our early warning system.
Intelligence requirements:
- What distribution methods are employed?
- Which vulnerabilities are exploited?
- Any observable patterns in the network traffic associated with the exploitation?
- Any observable patterns in the infrastructure utilised by the threat actors?
- Can any signatures be identified or extracted from the malware?
Establishment of Early Warning Systems
To proactively respond to emerging cyber threats, the establishment of early warning systems is imperative. These systems leverage observable signals and threat indicators to promptly detect potential cyber attacks, enabling organisations to take proactive defensive measures. To dive deeper into this, check out my blog post: https://robindimyan.medium.com/early-warning-intelligence-how-to-predict-cyber-attacks-1299af2dada3
When it comes to cyber crime intelligence, there are two approaches to constructing an Early Warning System (EWS). The first approach involves monitoring actor-centric observables, which proves highly fruitful when specific actors are of concern. By continuously surveilling these observables, one can meticulously track their activities. An analyst well-versed in the actor’s past can then piece together the information, enabling a confident prediction of an attack.
Drawing upon an example I previously shared: https://robindimyan.medium.com/profiling-and-cyber-threat-intelligence-3-9253e0371b56
Sign-1: A reputable data broker advertises a combolist for a renowned cryptocurrency exchange website. — (Risk Score: 2)
Sign-2: A threat actor who is known to provide SIM cloning / 2FA bypass services was observed contacting with the aforementioned data broker. — (Risk Score: 3)
Sign-3: Some recently registered domain names are utilizing an email address associated with the threat actor. — (Risk Score: 1)
Accordingly, if only the Sign-2 event occurs, the probability of a similar attack occurring is 3/6, ie 50%. If Sign-1 and Sign-2 events occur together, this means that this attack will occur with a 5/6, 83% probability. Of course, the numbers given here are completely up to you.
The second approach involves monitoring campaign observables, which are typically technical patterns inferred from previous intrusion analyses. Observing these early steps of an attack can help you identify the infrastructure, distribution and exploitation attempts associated with an ongoing campaign. Although in this approach the confidence level is higher, the prediction window is relatively shorter.
To quote another example from my previous post:
As a technical example, let’s look at the Leery Turtle campaigns. When these attacks were investigated, some characteristics were discovered in the C2 servers used in the attack. The following signs were defined for the observed characteristics.
Purchase of a new domain with the same pattern as Leery Turtle, containing at least two of the words google, drive, cloud, share, upload. (Sign 1: potential Leery Turtle domain)
Having ports 80 and 8080 open at the same time on the server directed by the domain name. (Sign 2: potential Leery Turtle host)
A domain/server was tagged as “Leery Turtle” when both of the conditions we defined met simultaneously. Then, customers were informed that attacks could come from those IP addresses and domain names. After a while, one of these domains was indeed used in a Leery Turtle attack.
More EWS examples here: https://robindimyan.medium.com/early-warning-intelligence-how-to-predict-cyber-attacks-1299af2dada3
I hope you liked this blogpost.
See you in the next one!
